Madison Valleywood sounds like a character from the next John Waters’ film, but it is actually a nickname given to the United States government’s latest attempt to combat ISIS online. Despite what may be the popular conceptions up to this point, ISIS is not reaching out and causing havoc at high levels through cyber terrorism. In order to understand what is and can be done to defeat ISIS online, it is important to have a general understanding of ISIS and how it works.

What Is ISIS?
ISIS is a terrorist organization that occupies large portions of Syria and Iraq, and has declared its intentions to create an Islamic world which ISIS would rule. As of 2016, ISIS has about eight million civilian subjects and several sources of income to fuel its efforts. Some of the more lucrative recurring sources of ISIS income include:
- Income tax on its people
- Oil revenue of around $1 million to $3 million per day
- Money stolen from the banks and governments ISIS defeats
The primary stated goal of ISIS is to bring down the Western World and replace it with Islamic rule, ISIS style. ISIS is smart enough to know that if it wants to defeat the Western World, it will have to become proficient in cyber terrorism. When you take an objective look at what ISIS has been able to accomplish so far online, the future does not look bright for this terrorist organization.
The ISIS Online Threat
It is important for people to remember that just because ISIS takes credit for a major online security breach does not necessarily mean that ISIS actually committed the breach. Despite the availability of money and recruits with technical backgrounds, ISIS’ Internet capabilities are extremely limited. To this point, ISIS has only been able to:
- Use social media to recruit new members and send out threatening messages to the Western World
- Hack websites with weak security protocols
- Take advantage of lapses in online security for larger websites and exploit those weaknesses
Right now, the online capabilities of ISIS rival those of a group of hackers angry at the world. While ISIS has been able to hack into low level government websites and some American banks, its ability to hack credit card user databases is commonplace among other high level hacker groups.

Where ISIS really shines online is its use of social media to recruit new members, arrange attacks using lone attackers, transfer funds to groups around the world, and send video messages to the world. As long as ISIS is able to reach mass audiences using social media, then it remains a threat.
What The Government Is Doing
Madison Valleywood is the nickname given to the government initiative to reach out to technology companies and social media websites to shut down the access ISIS has to the rest of the world. Companies such as Apple, Facebook, and Twitter are being asked to develop ways to combat ISIS online, and also being asked to follow government directives to remove the ability for ISIS to use the Internet in its operations.
n shows that there are still some areas where technology companies are unwilling to alter what they do to appease the government. However, Twitter has shut down hundreds of thousands of ISIS-related accounts and is constantly gathering data to shut down more accounts. If Madison Valleywood becomes a cohesive operation between the government and the companies of Silicon Valley, then that may be all of the technology the government will need to help defeat ISIS once and for all.
Find out more:
http://www.defenseone.com/technology/2016/01/americas-new-plan-fight-isis-online/125043/
https://www.flashpoint-intel.com/home/assets/Media/Flashpoint_HackingForISIS_April2016.pdf
http://blogs.berkeley.edu/2015/03/02/how-to-defeat-isis-and-why-it-probably-wont-happen/
http://www.cnn.com/2016/02/24/politics/justice-department-apple-fbi-isis-san-bernardino/
https://info.globalit.com/wp-content/uploads/2016/05/ISIS_TRAIL_OF_TERROR_16x9_992.jpg|https://info.globalit.com/wp-content/uploads/2016/05/external.jpg
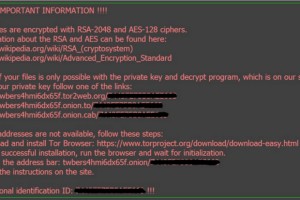
Case Studies


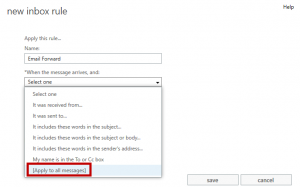




 The
The 
 Protect Yourself When Using Your Smartphone
Protect Yourself When Using Your Smartphone