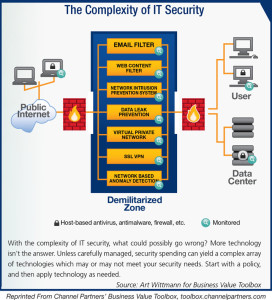
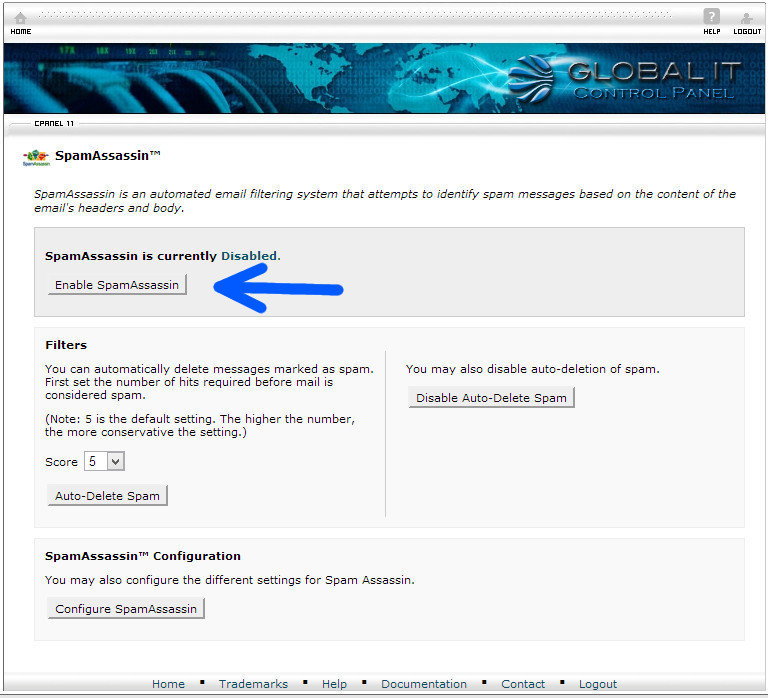
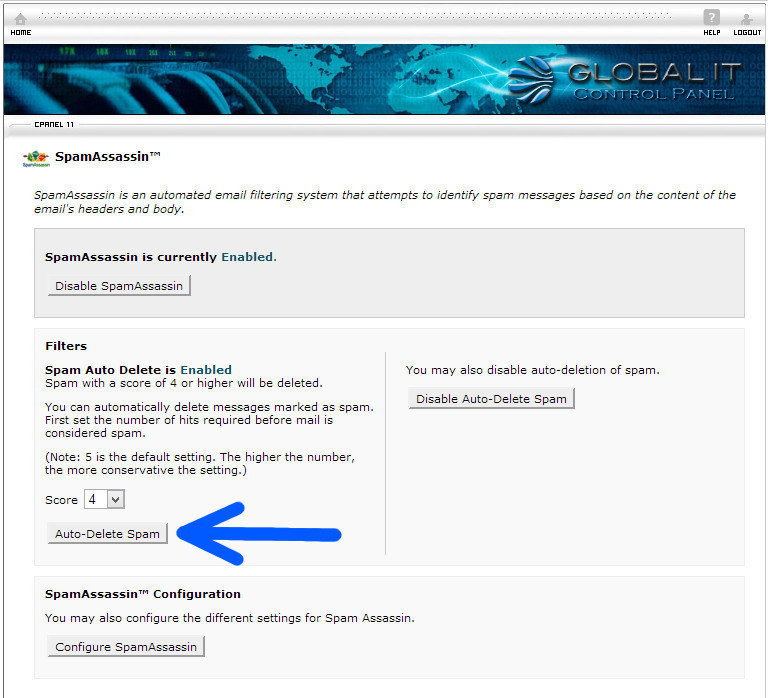
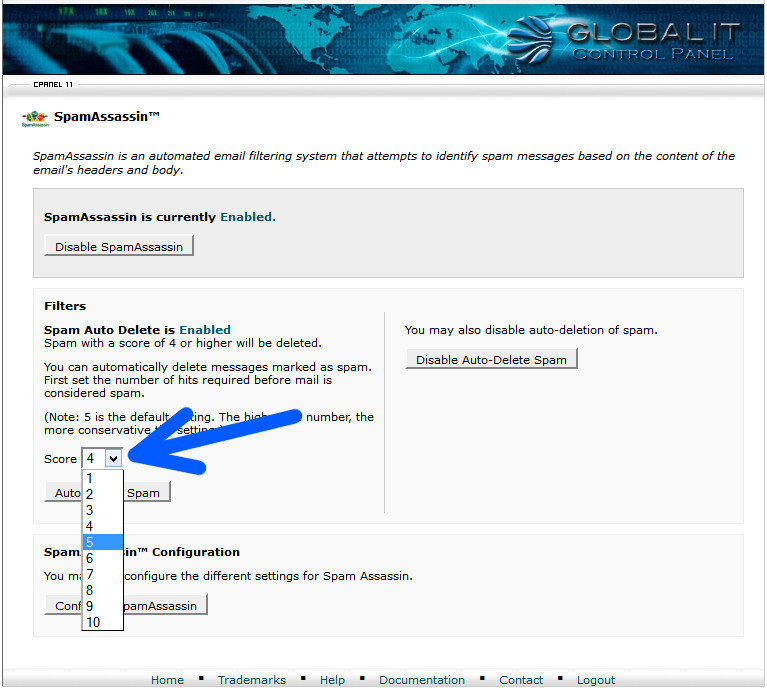
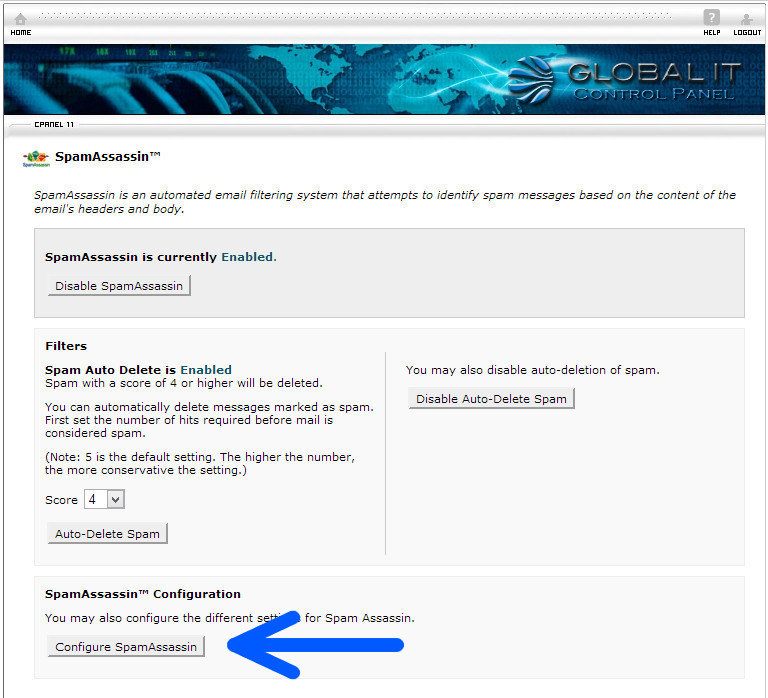
The Complexity of IT Security
Modern businesses – of all sizes – are becoming increasingly vulnerable to security breaches even as they enable their workforces with state-of-the-art technologies.
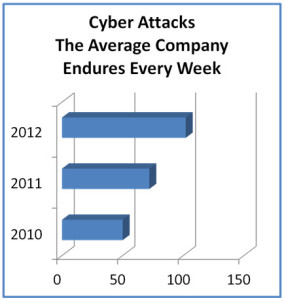
- Cyber attacks are up 100% since 2010.
- Cyber attacks can be costly. The average time to resolve a cyber attack is 24 days at an average cost of $591,780, or nearly $25,000 per day.
- The most costly cyber-crimes are caused by malicious code, denial of service, stolen or hijacked devices, and malevolent insiders.
Threat 1: Data Loss & Leakage
- Unintentional distribution

of sensitive data:- financial
- employee
- customer data
- intellectual property
- Due to:
- loss or theft of laptops or mobile phones.
- electronic transmissions, such as unencrypted emails, IM, webmail and file transfer tools, hacking, virus
Threat 2: Denial of Service Attacks

- DoS attacks flood a network with more traffic than it can handle, consuming bandwidth or server resources.
- Distributed DOS attacks use multiple systems to launch the offensive, making them difficult to shut down.
- DDOS attacks are growing in size – to more than 50GBps in 2012 ‒ and last more than 30 hours, according to data from Prolexic.
Threat 3: Malware
- Malicious software (aka malware) is unwanted software installed without consent.

- Examples include:
- viruses
- worms
- Trojan horses
- spyware
- Botnets, Zombie
Threat 4: Phishing/Social Engineering

- Cyber criminals use phishing and “social engineering” schemes to trick people into sharing personal information, such as:
- account information
- credit card data
- social security numbers
- passwords
- Phishing and social engineering are done typically with links to fill-in forms from:
- e-mails
- Websites
- social media
Threat 5: Human Error/Malevolence
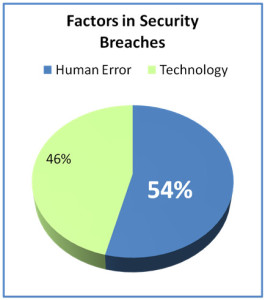
- More than 50% of security problems are due to employees or IT staff inadvertently:
- failing to follow procedure
- being careless
- lacking expertise
- Insiders or former insiders, such as disgruntled or malicious employees or contractors can be dangerous attackers because they know the organization’s:
- security codes and measures
- computers and applications
- actions that will cause the most damage
Understanding Data-Centric Security
Before you even think about technology, you need to determine who will be responsible for security. The development and communication of your security strategy is critical.
- Employee vulnerabilities
- Internet, cloud vulnerabilities
- LAN vulnerabilities
- Premises security
- Implement
- Minimum security codes and measures
- Define business and personal computer and applications use
- Define consequences for violating company security policies
- Educate users
https://info.globalit.com/wp-content/uploads/2013/09/cyber-attacks-on-rise.jpg|https://info.globalit.com/wp-content/uploads/2013/09/complexity-of-it-security.jpg|https://info.globalit.com/wp-content/uploads/2013/09/information-leakage.jpg|https://info.globalit.com/wp-content/uploads/2013/09/denial-of-service-attacks.jpg|https://info.globalit.com/wp-content/uploads/2013/09/malware.jpg|https://info.globalit.com/wp-content/uploads/2013/09/phishing-social-engineering.jpg|https://info.globalit.com/wp-content/uploads/2013/09/human-error-malevolence.jpg
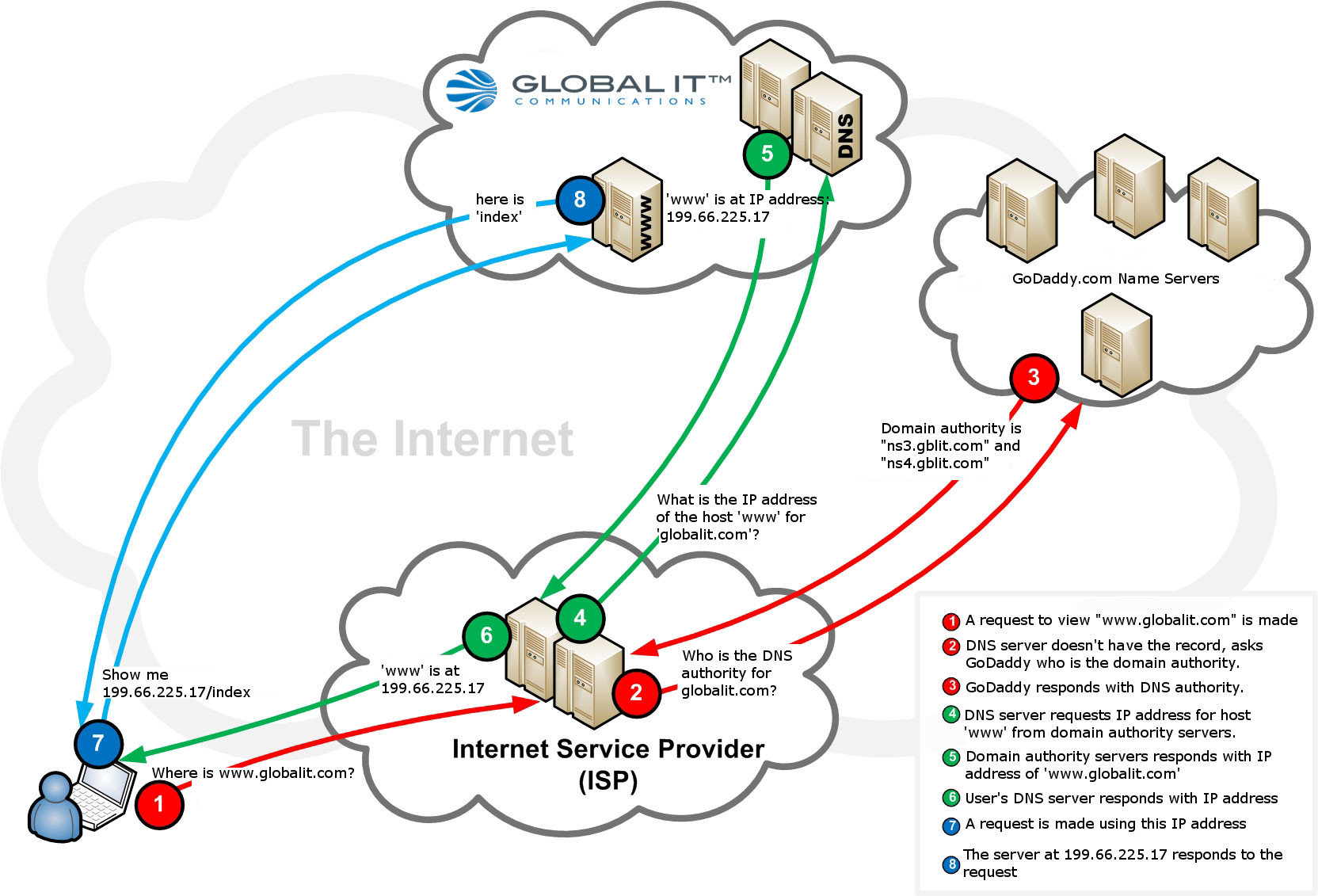
Internet Security|Webmaster


 Mobile has demonstrated that it is here to stay. As more and more users begin to utterly depend on their mobile device to connect them with the world, it has become even more essential for companies to institute an effective mobile strategy for their website. Since new mobile devices appear every day, web designers must figure out a way to make sure that their websites are compatible with every new gadget that shows up on the market. Responsive web design is one of the most popular methods of achieving this goal.
Mobile has demonstrated that it is here to stay. As more and more users begin to utterly depend on their mobile device to connect them with the world, it has become even more essential for companies to institute an effective mobile strategy for their website. Since new mobile devices appear every day, web designers must figure out a way to make sure that their websites are compatible with every new gadget that shows up on the market. Responsive web design is one of the most popular methods of achieving this goal.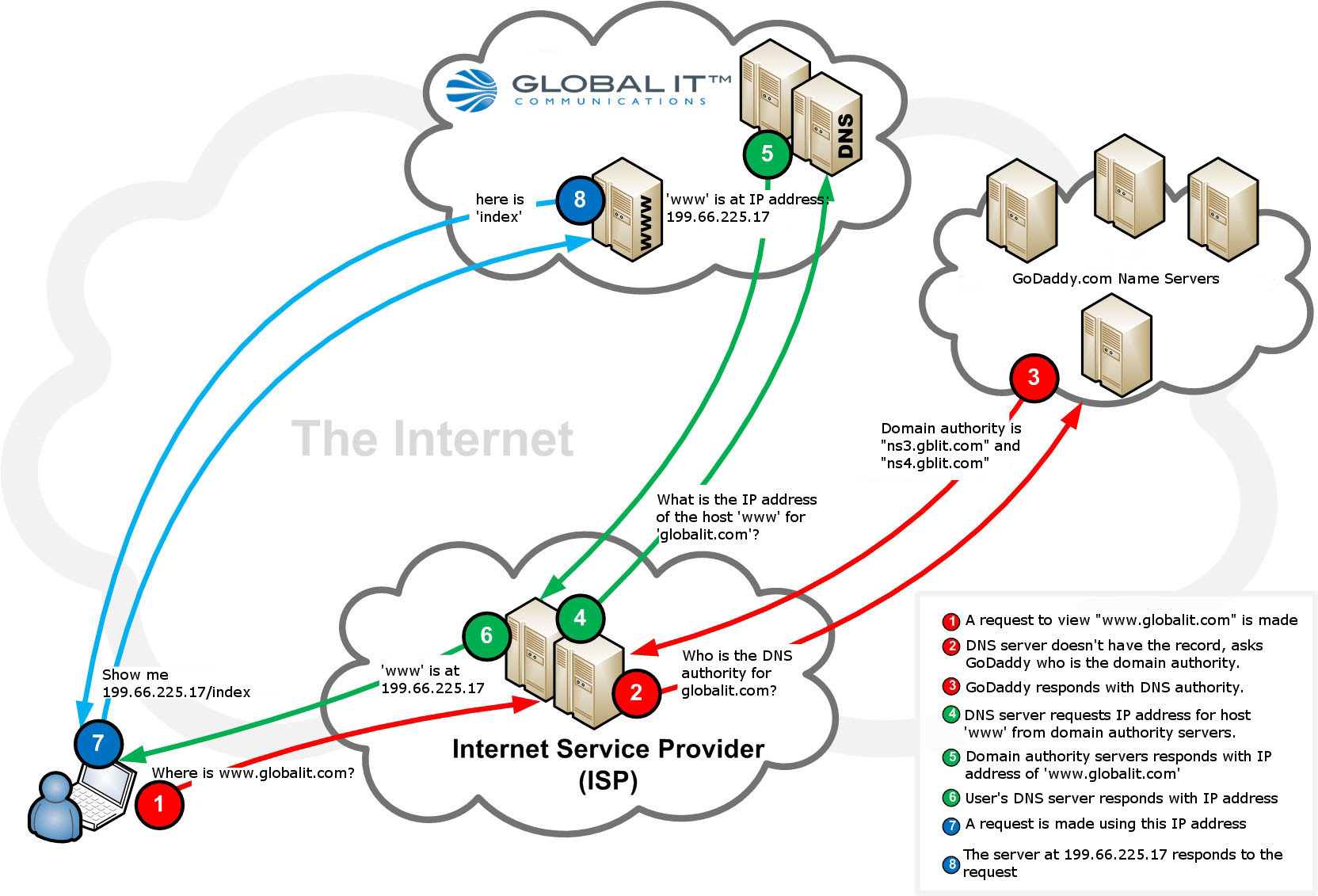


 If you have been contacted by a telemarketer informing that you have been sending out viruses or adware from your computer, this is a SCAM and we are recommending that you follow the following steps. This company is known to pose as Global Tech, Global PC or Global IT and saying that they are partnered with Microsoft.
If you have been contacted by a telemarketer informing that you have been sending out viruses or adware from your computer, this is a SCAM and we are recommending that you follow the following steps. This company is known to pose as Global Tech, Global PC or Global IT and saying that they are partnered with Microsoft.

 If you are one of the many SMB’s (small to medium business) considering switching to VoIP(Voice over Internet Protocol) as a telephone solution, you might be asking yourself, what is VoIP? Why do I need VoIP and how much does it cost?
If you are one of the many SMB’s (small to medium business) considering switching to VoIP(Voice over Internet Protocol) as a telephone solution, you might be asking yourself, what is VoIP? Why do I need VoIP and how much does it cost?
 With business owners focused on running their company, they have virtually no time to handle online marketing.
With business owners focused on running their company, they have virtually no time to handle online marketing. 
 Spyware and Adware are programs that are installed on a computer that perform operations that the user probably doesn’t want. Spyware is a program that was created for the purpose of collecting information and sending it to a designated entity. The information it gathers can be from which terms or phrases you are searching and which websites you are visiting, to personal and financial information like your date of birth, social security number, or credit card information. Adware has a different purpose. It will usually ‘pop-up’ advertisements in websites when you search for a specific term or phrase, or it may be an entirely separate pop-up window on your desktop that advertises something.
Spyware and Adware are programs that are installed on a computer that perform operations that the user probably doesn’t want. Spyware is a program that was created for the purpose of collecting information and sending it to a designated entity. The information it gathers can be from which terms or phrases you are searching and which websites you are visiting, to personal and financial information like your date of birth, social security number, or credit card information. Adware has a different purpose. It will usually ‘pop-up’ advertisements in websites when you search for a specific term or phrase, or it may be an entirely separate pop-up window on your desktop that advertises something.