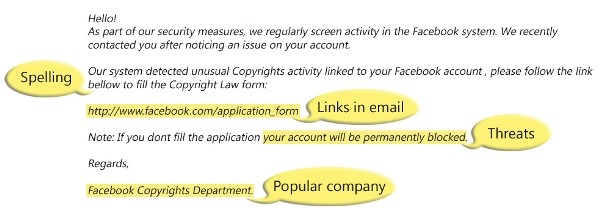
How Customer Reviews Affect Your Organic Rankings
How Customer Reviews Affect Your Organic Rankings
As a business, you want your online presence to stand out among the competition. One of the best ways to do so is by encouraging your audience to complete customer reviews online. As seen in Moz’s breakdown of local search ranking factors, there are a variety of things that contribute to your business’s visibility online. While it’s important to consider all of them, there are a few that stand out for business owners.
In addition to providing your business with valuable feedback, customer reviews will improve your ranking online. Businesses gain positive exposure online with consistent customer reviews while effectively boosting rankings through sites like Google+ and other online directories.
Google+
Reviews left on Google+ Local Pages help other potential customers in the area quickly refer to highly-rated businesses. With Google+, slow and steady is the key. Customer reviews that appear at a natural pace are less likely to be automatically removed and result in a higher organic ranking.
Third-party directories, like Yelp and TripAdvisor, are included in Google’s search for information about your business. Accumulating reviews in third-party directories will contribute to an increase in your organic ranking.
Top 5 Directories for Reviews
Among the vast number of directories available online, five, in particular, stand out as most beneficial when trying to improve your business’s organic ranking.
- Google+
Google+ is being used by more businesses than ever to connect with their audience and stay a part of industry conversation. With over 540 million monthly active users, businesses can count on their interactions with customers on Google+ to improve organic rankings for their site.
- Yelp
As one of the leading third-party review sites, Yelp reels in more than 47 million local reviews and 117 million unique visitors each quarter. Since it has become one of the leading review sites on the internet, businesses improve their chance of higher rankings when customer reviews are listed on Yelp.
- YellowPages
Although their big yellow books are no longer a popular resource, YellowPages.com remains alive and well as a source of information online. Including your business listing in the YellowPages will make your information available to over 3 million visitors monthly.
- Superpages
Averaging over 3.5 million page views per day, Superpages is another great listing option for businesses that want to improve organic search rankings. Since the website makes it easy for mobile users to peruse its pages, Superpages helps businesses reach more customers.
- Yahoo
As one of Google’s strongest competitors, Yahoo is an attractive option for businesses that want to improve their rankings. Each week, Yahoo earns over 2.2 million visitors, nearly half of which are search-related.
Valid Reviews are Essential
In order to improve your business’ organic rankings with integrity, valid reviews are essential. The use of fake reviews in an online forum or directory will only serve to hurt your business’ image. Fake reviews are:
- Easy to Spot
Consumers these days are savvy. The increased amount of time spent online daily has increased general consumer awareness of red flags, allowing fake online content to be spotted easily. Some tell-tale signs of a fake review include a focus on only good qualities of a company or product, multiple raving reviews around a certain date, or a salesman-like tone to the review.
- On Their Way Out
With major search engines like Google and Yahoo taking a decided stance against black hat SEO practices, fake reviews continue to be a source of frustration provoking an active attempt to eliminate them. There will soon be (if not already) strict consequences in search results for businesses that publish fake reviews.
- Caught By Directories
As the computing world transforms to include better, more intuitive technology, it’s becoming easier for directories to effectively weed out fake reviews. Directories are better able to spot red flags, like reviews originating from the same IP address or an unnatural burst of reviews all at once, and respond accordingly. Businesses are at risk of everything from removed listings to complete bans from service.
- Harmful to the Trust-Building Process
Improving your business’ organic rankings is an important part of growing your company and must be treated with integrity. Publishing fake reviews about your services or products is bound to get uncovered at some point. When it does, what you’ve truly lost is the ability to keep your customers’ trust.
Earn Customer Reviews the Right Way
Receiving a steady flow of customer reviews is your business’s reward for providing unrivaled service. Instead of soliciting reviews with incentives, be consistent with your business listings and make reviews easy for your customers.
- Make Reviews Easy
It’s much easier to earn a customer’s review of your business when the process is simple, takes only a few seconds, and is outlined clearly. You’re more likely to gain a customer review if you send instructions in an email, list instructions on your website, or send a sample review that your customer can quickly edit and add to the listing of their choice.
When requesting a review, be sure to ask questions about your customer’s needs, how your business met their needs and their satisfaction level with your company.
- Be Consistent
To improve your organic rankings, maintain a professional online presence, and reduce confusion about your company. It’s essential to be consistent. When entering information into business listings online, first develop a master copy with your company’s contact, website, and profile information.
Use this information on each one of your business listings to prevent changes in capitalization or punctuation. Before a listing goes live, re-check your draft to ensure there are no typos and your site’s link is working properly. Inconsistency can damage your credibility with search engines.
Local Marketing Prevails
As far as Google is concerned, local marketing is a large part of the future of search. In fact, Google’s push for an emphasis on local marketing is allowing businesses the opportunity to reach out to the customer base right in their backyard. Google’s ongoing changes to its search algorithm continually favor local search and local businesses.
Reports indicated that as many as half of all searches on Google are made with the intent to find something local. Naturally, this number increases significantly for mobile users who are in need of information on the go. As a result, local marketing strategies are becoming more defined as businesses try to tap into their local audience.
Tips, Insights, and Trends for Local Marketing
Long before Google began to put emphasis on local search, local SEOs knew that the importance of the local search for businesses would bloom. One of the top tips for businesses includes building a complete and accurate listings presence.
Seasoned online marketing professionals are predicting increased use of location-based marketing platforms, such as Google Places and Google+ Local, and will place further emphasis on the importance of building the presence of a listing.
Statistics report that approximately 91% of adult mobile phone users keep their phone within arm’s reach. With apps like Google Wallet and PayPal, virtual commerce is becoming seamless, allowing consumers to make instant purchase decisions from the convenience of their mobile device.
Improving your business’s organic search ranking through customer reviews is a great way to increase your visibility online while expanding your reach to new customers. In order to be effective, your business’ marketing campaign needs to include a plan to obtain customer reviews online while maintaining the presence of a consistent listing. If you need help improving your organic search rankings, contact GLOBAL IT for more information at (877) 822-5565.
https://info.globalit.com/wp-content/uploads/2013/12/fastest_broadband_internet_connection_in_cambridge.jpg
Online Marketing|Webmaster


 Net Neutrality and What This Means to You
Net Neutrality and What This Means to You


 How Customer Reviews Affect Your Organic Rankings
How Customer Reviews Affect Your Organic Rankings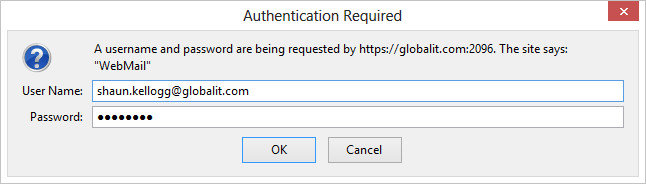

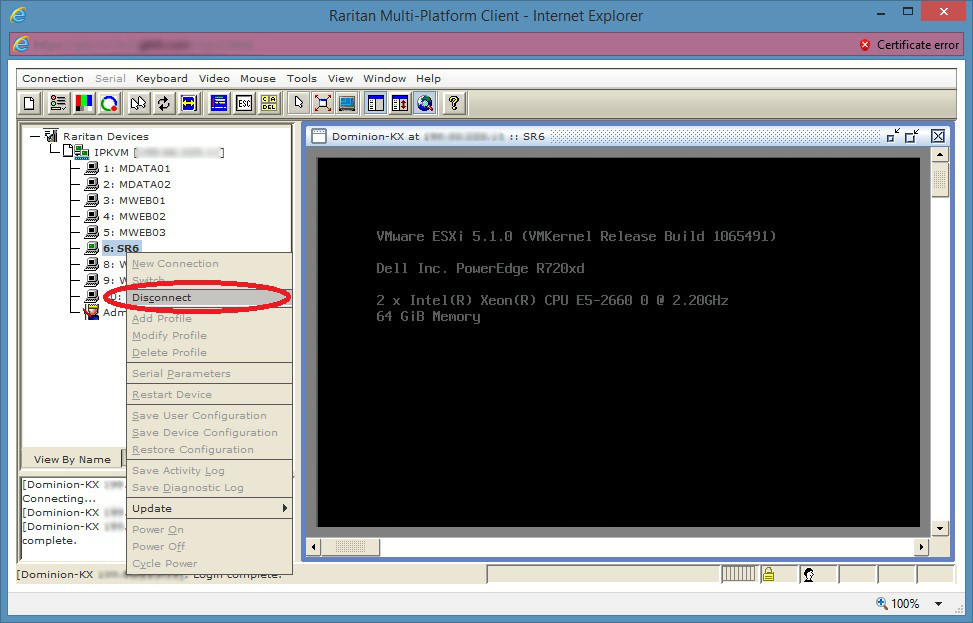






 Selecting a personal image to be used for business purposes poses the question; business professional or business casual attire?
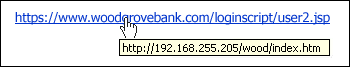
Selecting a personal image to be used for business purposes poses the question; business professional or business casual attire? There are two types of common threats most non technical staff will encounter.
There are two types of common threats most non technical staff will encounter.