Global IT has been serving the hospitality industry for more than 11 years and our IT leadership experience dates back to 1996. Global IT hospitality product and services portfolio spans from major hotel chains to exclusive Beverly Hills and beachfront hotels in Southern CA.
Through its wide range of services, Global IT fortifies the hospitality industry with a unique set of products and services that enable hotels the opportunity to deliver a premium guest experience.
Quick links:
Hotel # 1 – Four Points by Sheraton – Los Angeles
Hotel # 2 – The Malibu Beach Inn – Carbon Beach
Hotel # 3 – Mr. C Hotels – Beverly Hills
Hotel #1
Scope of Services:
This hotel is located in a highly competitive market that services the Los Angeles International Airport. With 566 rooms and 6,000 square feet of meeting space, this hotel is one of the busiest in the area.
At the time the hotel was overspending on IT services and the IT management company was falling short of providing the level of support a large volume hotel needed. Lack of support eventually leads to the potential of lost revenues, less than satisfactory customer satisfaction, IT setbacks, confusion, and frustration from guests, employees, and management. That’s when Global IT was asked to step in. The Global IT managed IT solutions along with our expert-level knowledge of service provider infrastructure allowed Global IT to deliver the type of service that a large-scale hotel in a highly competitive market demanded.
Working with the hotel’s General Manager, Director of Operations and Chief Engineer, Global IT was tasked to identify key areas where the IT infrastructure was failing, create a short and long term action plan along with budgeting to help get the IT infrastructure up-to-date and eliminate unnecessary services from other vendors.
Global IT immediately went to work. The first step was to audit existing vendors and technologies and then implement immediate easy changes in the way the hotel managed its network. By utilizing Global IT monitoring services, the hotel was given the capability to quickly identify bottlenecks in the network reducing downtime. Our proprietary remote management service allows access to any device connected to the network for troubleshooting issues and network changes.
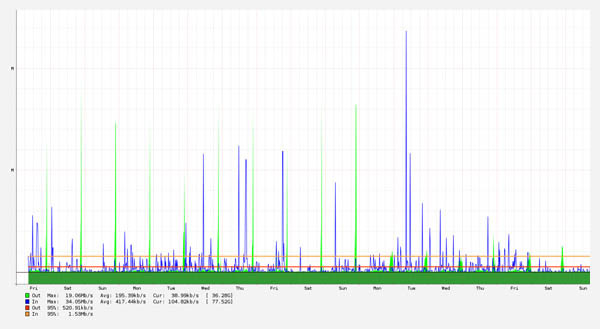
Network stabilization was one key element missing from the hotel. Now that they have regained their confidence in the network they have proceeded with adding additional guest services including IPTV, expanding their guest network to include increased bandwidth, and now offering new services for their meeting rooms and pool areas.
Hotel #2
Scope of Services:
Located on one of the most exclusive beachfront properties in the Southern California this hotel is one of the most highly sought-after locations for hotel stays in Los Angeles.
One of the biggest areas of dissatisfaction with the hotel was the type of service local Internet carriers provided. Local carriers simply did not understand the bandwidth availability needs of the hotel, only offering Ethernet over Copper solutions for the beachfront property. Global IT was asked to provide an alternative to the EOC solution that would increase the uptime and dependability needed for their network.
Working with major carriers and local municipalities, Global IT was able to install fiber solutions that delivered the bandwidth capacity and dependability the hotel needed for their guests. By understanding client requirements and being a beachfront property. Global IT deployed industry-leading networking devices and specialty configurations that would comfortable allow this hotel reliable VoIP and remote connectivity for operations.
Once the hotel had the capability to serve their guests, they needed a wireless solution that could perform up to the standards that their guests had come to expect. Global IT designed a wireless solution utilizing technology from Adtran Inc. with carrier-grade hardware to guard against corrosion from the salted air. The Adtran technology allowed for seamless connectivity for high-end guests without limitation.
The hotel faced a new challenged when they decided to expand their offices to a new location a few miles away on the hillside of Malibu.
Their new offices could not get the consistent quality of service needed to deliver IP phone service and remote access service between locations. Global IT was asked to step in and help with this issue. Using their existing Global IT circuit that was previously installed at the hotel, Global IT delivered a private MPLS circuit from the hotel to the new offices and installed enterprise networking devices. Controlling both ends of the virtual circuit gave Global IT the ability to add traffic shaping along with the quality of service to the site. The current IT team had contracted with another cabling company. Through our proprietary monitoring systems,
Global IT identified numerous cable problems and recommended ideal internal LAN configuration adjustments to help resolve ongoing LAN connectivity problems. Global IT Engineers were able to design a solution that delivered the service they were looking for.
Hotel #3
Scope of Services:
One of the most revered hotels in Beverly Hills, this hotel has developed a reputation for its luxurious style, quality, and service.
So when their local IT service provider was not meeting the expectations and standards set by the hotel, Global IT was asked to step in and deliver the type of service the hotel prides itself on.
One of the first items on the list was to document the hotel’s complete infrastructure. With no real documentation on service and Service Level Agreements, Global IT had to manually discover all the intricacies of the network including hardware, software, and wiring. Working with General Manager, CFO, Building Engineer, and hotel staff Global IT created a comprehensive list of wants and needs to go along with infrastructure documentation.
Next, Global IT created a prioritized task list to address outstanding weaknesses in the IT infrastructure including; backups, out-of-date licensing, legacy hardware, monitoring, and remote management. The hotel’s network was incorrectly configured and out of hard drive space. Global IT correctly and efficiently configured their network, providing a dedicated backup system and allocated more hard drive space. The backup system ensures no downtime in the event of a natural disaster. Current licenses, upgraded operating systems, hardware, software, and anti-virus system were all purchased, installed, and are currently being managed. Servers, storage devices, and terminals are all remotely monitored and managed.
Global IT also completed a migration from Google email to Microsoft Exchange. With careful planning and organization, the migration was a smooth process with only minor delays.
With gained confidence from the hotel, Global IT was asked to take part in the building of new office suites at a nearby location. Managing the infrastructure aspect of the build, Global IT was successfully able to install and relocate the new admin offices. Global IT was asked to pick up pieces where other vendors had fallen short.
https://info.globalit.com/wp-content/uploads/2014/08/monitoring.jpg|https://info.globalit.com/wp-content/uploads/2014/08/fps-sheraton1.jpg|https://info.globalit.com/wp-content/uploads/2014/08/hotel-malibu.jpg|https://info.globalit.com/wp-content/uploads/2014/08/hotel-bh.jpg
Case Studies|IT Services










 Best Practices for Cash Register and PoS Security
Best Practices for Cash Register and PoS Security 


 Best Remote Desktop Access Security Configuration
Best Remote Desktop Access Security Configuration  Many businesses outside of the US are looking to expand their markets and offer their products to US consumers. This is especially true if these businesses are primarily selling their products through an ecommerce platform. There are a few challenges involved in bridging that gap to online US sales. Most of US consumers are weary of making purchases from international ecommerce sites because they are concerned with lack of consumer protection, unsafe transmit credit information and unexpected taxes or fees on purchases. Colocating in the US is the first step to establishing a local online presence and increase buyer confidence.
Many businesses outside of the US are looking to expand their markets and offer their products to US consumers. This is especially true if these businesses are primarily selling their products through an ecommerce platform. There are a few challenges involved in bridging that gap to online US sales. Most of US consumers are weary of making purchases from international ecommerce sites because they are concerned with lack of consumer protection, unsafe transmit credit information and unexpected taxes or fees on purchases. Colocating in the US is the first step to establishing a local online presence and increase buyer confidence.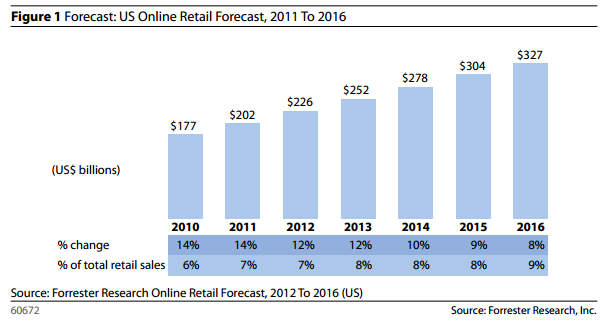

 When deciding whether to choose hosting on-site versus using a colocation facility, there are several factors to consider. Some of these factors include:
When deciding whether to choose hosting on-site versus using a colocation facility, there are several factors to consider. Some of these factors include: