Global IT has been recommending and developing responsive, mobile-friendly, websites for several years.
Read: Why Moving Toward Responsive Web Design Has a Direct Effect on Your Marketing (May 2013)
Having a website that is compatible across all platforms (desktop, tablet, and smartphone) is no longer a choice, but a necessity. Following are 10 reasons why you should be planning to move toward a mobile-friendly website if you haven’t done so already.
***The last reason listed at #10 will have the most impact on the future of online presence for EVERY industry…and this change is coming SOON.***
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″]1.) Mobile friendly websites give you a competitive advantage.[/googlefont]
[box style=”2″]”Here is the bottom line for B2B marketers:
The mobile experience is now directly impacting your fundamental online marketing success and affecting metrics such as visibility and traffic.
Providing a favorable mobile experience is absolutely required to continually engage prospects and drive leads and sales.
B2B decision-makers are using mobile devices across all phases of the buying cycle and throughout the day (including at work).
Take a look at your website analytics data. Even if mobile traffic isn’t a huge device segment today, it is growing and will continue to do so.
Get ahead of this curve. Start embracing our multi-screen world. Turn mobile marketing into your competitive advantage… today.” SearchEngineLand[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]2.) Mobile friendly websites increase customer satisfaction.[/googlefont]
[box style=”2″]”In a trend which Forrester Research refers to as the ‘mobile mind shift’, the rapid increase in the use of smartphones for day-to-day tasks fuels increasingly demanding customer expectations. According to Forrester, 62% of customers who look for a company on their smartphone will expect to find a mobile-friendly website; 42% expect a company to have a mobile app and 23% expect their experience to be relevant to context (e.g. location).
Expectations go beyond just having a mobile presence; customers expect you to provide them with a great mobile experience. Customers love the ease and speed of well-designed mobile platforms while faulty links, slow-loading pages, and site errors will only serve to frustrate users. Also, as a result of user experience errors, Google now demotes mobile web page rankings in its search results, making it harder for mobile customers to find your site.
There’s a direct correlation between the quality of service you deliver and customer loyalty but a company will only get these benefits if they deliver a quality mobile experience.” UserZoom[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]3.) Mobile friendly websites give your business more credibility.[/googlefont]
[box style=”2″]”Findings show that purchase decisions made by local consumers are more impacted by websites now than in 2014.
-More consumers contact a business if it has a website (36% vs 32%)
-More consumers say they are put off by an ugly website (9% vs 5%)
-Fewer consumers will use a business that doesn’t have a website (21% vs 27%)
And…having a smart website gives local business credibility in eyes of consumers.” BrightLocal[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]4.) 59% of smartphone users expect companies to make their websites mobile-friendly.[/googlefont]
[box style=”2″]
1. Within 2 years, there will be 3B+ smartphones in use. The average user spends 4-5 hours per day on mobile. (Source)
2. 59% of smartphone users expect companies to make their websites mobile-friendly. (Source)
3. Mobile will account for 50% of all digital ad spend in 2016 (worth $100B). (Source)
4. Mobile accounts for 35% of all retail eCommerce transactions. (Source)
5. 37% of purchases are made after the users viewed the retailer’s site on multiple devices. (Source)
6. Of that 37%, 69% were finished on desktop. (Source)
Branch[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]5.) There are over 200 million smart phone users in the United States and the numbers are increasing every day.[/googlefont]
[box style=”2″][responsive]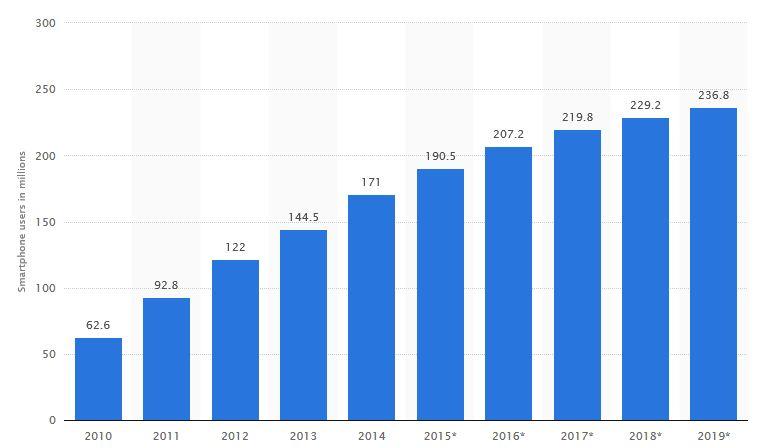 [/responsive]Statista[/box]
[/responsive]Statista[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]6.) Failing to move to a mobile friendly website can result in a loss of business opportunity.[/googlefont]
[box style=”2″]”Your bounce rate measures the percentage of users that viewed one page on your site and then left. A high bounce rate indicates a problem keeping users engaged on your website. If your bounce rate is significantly higher on mobile devices than on desktop devices, it would indicate a likely issue with the way your site displays on a mobile device.
Session duration measures the average amount of time each user remained on your website. Again, a much lower session duration on mobile devices would indicate that your users are getting frustrated quickly and leaving. Not seeing much in terms of mobile and tablet traffic in your report? The most likely reason is most likely because your site isn’t mobile-friendly, you’re not getting the search or social referral traffic you would be getting if it was.
[68% of US adults] own a smartphone, and that number has only continued to grow…would you really want to miss out on [68%] of your potential customer base?!” SearlesGraphics[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]7.) 77% of mobile searches are at home or work where a PC is available.[/googlefont]
[box style=”2″][responsive]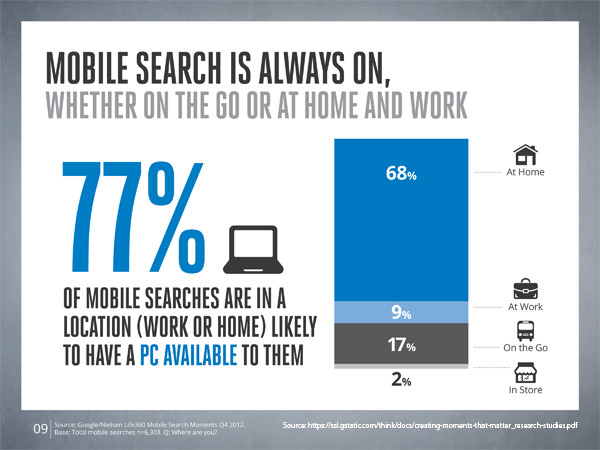 [/responsive] Gstatistic.com[/box]
[/responsive] Gstatistic.com[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]8.) Having a mobile friendly website is worth the investment.[/googlefont]
[box style=”2″]Whilst you might need to spend some money to get a top quality web designer to set up a responsive website for you, most website owners will tell you that it is money well spent. As well as preventing unhappy customers from shopping elsewhere it will mean less maintenance will be required in the future. Business.com[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]9.) Google finds the need to have a mobile friendly website critical for users.[/googlefont]
[box style=”2″]”Mobile is critical to your business and will continue to be so – whether you’re blogging about your favorite sports team, working on the website for your community theater, or selling products to potential clients. Make sure visitors can have a good experience on your site when they’re visiting from their mobile devices!” Google[/box]
[googlefont font=”Lalezar” size=”25px” margin=”20px 0 10px 0″ color=”green”]10.) Google will soon be releasing a mobile index that will only display mobile friendly websites.[/googlefont]
[box style=”2″]”Currently, Google has a single index of documents for search. Google’s Gary Illyes announced they plan on releasing a separate mobile search index, which will become the primary one. Google is going to create a separate mobile index within months, one that will be the main or “primary” index that the search engine uses to respond to queries. A separate desktop index will be maintained, one that will not be as up-to-date as the mobile index.” SearchEngineLand[/box]
Now that you know the importance of having a mobile-friendly website, it’s time to check the mobile-friendliness of your website. You can do so by visiting https://www.google.com/webmasters/tools/mobile-friendly/.
If you test your website and it does not pass Google’s specifications for mobile-friendliness, you have two choices.
- Edit your existing website to fit Google’s specifications.
- Redevelop a new website.
If your website is more than two years old, chances are your best option would be to redevelop a new website. If you are interested in having Global IT provide a quote to make sure your website is mobile-friendly, you can call us at 562-698-2500 opt. 2, or submit your request to design@globalit.com.
Read more about Global IT Web Design at http://globalit.com/website-design.
https://info.globalit.com/wp-content/uploads/2016/10/google-mobile-friendly-featured-image.jpg
https://info.globalit.com/wp-content/uploads/2016/10/google-mobile-friendly-featured-image.jpg|https://info.globalit.com/wp-content/uploads/2016/10/over-200-million-smartphone-users-in-the-us.jpg|https://info.globalit.com/wp-content/uploads/2016/10/77-percent-of-mobile-searches-are-at-home-or-work-where-a-pc-is-available-source-copy.jpg
Online Marketing|Web Design







 What would you do if the government said that the contractor who built your home must have a spare set of keys to the home, and there must be a door built on your home that only the contractor could access? Would you feel safe? How would you feel knowing that law enforcement could secretly enter your home any time it wanted simply by serving a warrant on the contractor who built your home?
What would you do if the government said that the contractor who built your home must have a spare set of keys to the home, and there must be a door built on your home that only the contractor could access? Would you feel safe? How would you feel knowing that law enforcement could secretly enter your home any time it wanted simply by serving a warrant on the contractor who built your home? The terrorist attacks in late 2015 in San Bernardino, California brought the issue of encryption to the forefront because of the very public battle between Apple and the F.B.I. According to the
The terrorist attacks in late 2015 in San Bernardino, California brought the issue of encryption to the forefront because of the very public battle between Apple and the F.B.I. According to the  What this debate boils down to is that some factions in the government want to force manufacturers to make user data accessible, and other factions want to preserve privacy. If the Compliance With Court Orders Act is passed, companies like Google would have to redesign products such as Gmail to make user data accessible. Right now, Google cannot read user emails at all unless Google has access to a user’s computer. If this bill becomes law, Google and anyone else who can get past the weakened Gmail encryption could read any user’s email.
What this debate boils down to is that some factions in the government want to force manufacturers to make user data accessible, and other factions want to preserve privacy. If the Compliance With Court Orders Act is passed, companies like Google would have to redesign products such as Gmail to make user data accessible. Right now, Google cannot read user emails at all unless Google has access to a user’s computer. If this bill becomes law, Google and anyone else who can get past the weakened Gmail encryption could read any user’s email.