Case Studies
Category: Case Studies
Best Computer Support!
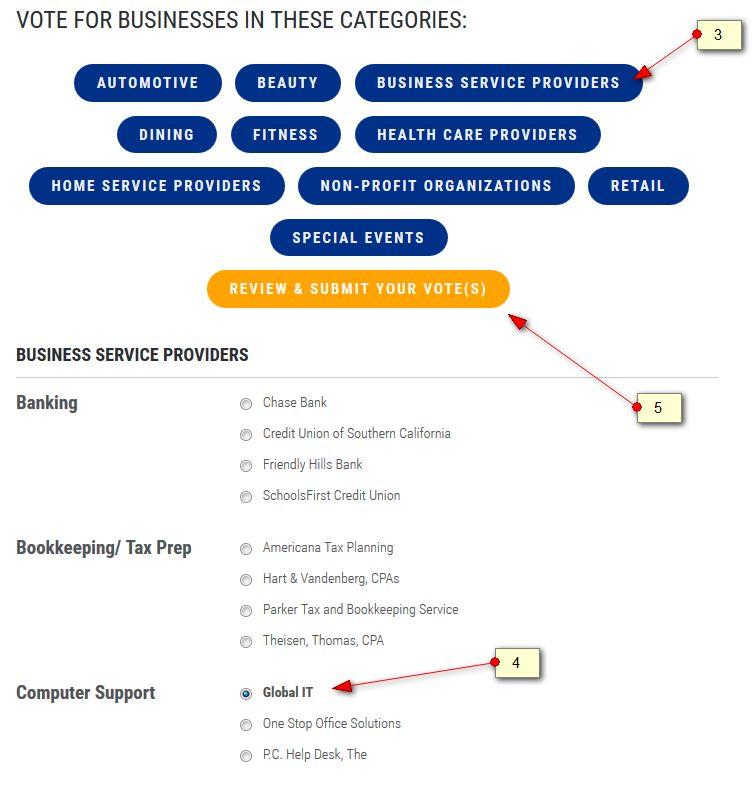
Global IT won the award of Best Computer Support presented by The Whittier Area Chamber of Commerce & City of Whittier.
Recognized at ‘Spotlight on the Whittier Chamber’ Annual Installation and Awards Ceremony on April 7 at the Ruth B Shannon Center of the Performing Arts.
Global IT’s President, Tony Willimas, VP of Marketing, Jayme Williams and Marketing Administrator, Stephanie Downs; attended the event and received the award.
“It’s an honor win Best Computer Support and to be recognized as the best by our local community and clients. A huge thank-you to everyone who voted for us, it’s a privilege to receive such an award.” Tony said.
The evening was filled with networking, food stations and there was even a cocktail hour.
All award winners were nominated and voted for by the local Whittier community.
The Global IT team thanks everyone who voted and is honored to be Best Computer Support for 2016.
https://info.globalit.com/wp-content/uploads/2016/04/IMG_3048-e1460156053806.jpg|https://info.globalit.com/wp-content/uploads/2016/04/IMG_3053-e1460156213543.jpg
Case Studies
5G Closer Than you think

From a technology standpoint, 2017 looks like it is going to be the start of another revolution. In 1991, many people thought mankind had reached the pinnacle of technology with the introduction of the mobile phone. But as we know now, that was only the tip of a very big iceberg.
With the introduction of the first widely available 1G network in 1991, the foundation was laid for making the Internet of Things (IoT) a reality. But first, we need wireless Internet network to get us there. That network is 5G.
What Is The Internet Of Things?
The IoT allows a car to talk to a parking ramp to determine if there are any parking spaces available, and it allows a streetlight to let the city’s works department know when a bulb is out. The goal that connectivity experts have is to create a world where everyone and everything can talk to each other about whatever they want or need to say. It will help to speed up commerce, advance medicine, and make the world a better place. But in order for the IoT to be a reality, the world needs 5G.
What Is 5G?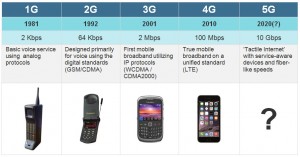
Right now, the world operates under a 4G network that allows communications to operate at speeds that are 10 times faster than the old 3G networks. In theory, 5G will expand the bandwidth and speed of 4G by 100 times. It will utilize radio frequencies and static signals to create a wireless network that will offer a capacity increase for data and communications by between 30 and 50 times larger than anything we have now. In short, 5G will enable the world and everything in it to be able to talk to each other in real time.
Didn’t We Just Get 4G?
MarketStrategies.com shows us that the appearance of 5g at this point in history is not unusual. A full 4G network was introduced around 2010, and a new network upgrade has been occurring every 10 years like clockwork. But 5G represents more than just an upgrade to the existing cellular network. It is a complete overhaul of the existing system that will use bandwidth that had previously been out of range for cell companies to utilize.
Another reason it is important to implement 5G as soon as possible is because the needs of the cellular communications industry are exceeding the abilities of the existing networks. Technology is advancing at a pace well beyond what mankind is used to, and 5G has to happen soon in order to meet the needs of a rapidly growing industry.
Companies like AT&T are a little more optimistic about the general availability than others. AT&T insists that 5G will be available in 2017, but that is only part of the truth. The implementation of 5G will begin in late 2016, but it will not be completed until 2020. Between 2016 and 2020, there will be sub-versions of the 4G network (4.25, 4.50, 4.75, etc.) that will lead up to the final 5G network.
Communications experts are expecting the 5G network to undergo a constant stream of updates and upgrades, so it is quite possible that we will not ever see a finished version of the 5G network. But it does look like your car will be talking on its own to the parking ramp at work by 2020.
Technology must keep evolving if it is going to meet the growing demands of mankind. The fully-operational 5G represents only the beginning of a world where man and machine may wind up living together in harmony. If you think about it, the whole idea sounds like an interesting science fiction movie. But the exciting part is that it is all going to become reality.
https://info.globalit.com/wp-content/uploads/2016/04/2015-03-5g-fig1.jpg|https://info.globalit.com/wp-content/uploads/2016/04/iStock_000049614472Medium1.jpg|https://info.globalit.com/wp-content/uploads/2016/04/5G-Technology.jpg
Case Studies
Security Protection: Top Concern for Mobile Payments
 The Federal Reserve Board estimates that 87 percent of all American adults own a cell phone and 71 percent of those phones are Internet-enabled smartphones. The convenience of mobile access to the Internet means that more users are going to start shopping through their phones, and the numbers show that the trend is increasing. In 2012, smartphone users who used their phones for online banking was at 29 percent, which grew to 33 percent in 2013 and then to 39 percent in 2014. It is time that consumers took their mobile computing security seriously.
The Federal Reserve Board estimates that 87 percent of all American adults own a cell phone and 71 percent of those phones are Internet-enabled smartphones. The convenience of mobile access to the Internet means that more users are going to start shopping through their phones, and the numbers show that the trend is increasing. In 2012, smartphone users who used their phones for online banking was at 29 percent, which grew to 33 percent in 2013 and then to 39 percent in 2014. It is time that consumers took their mobile computing security seriously.
 Paying For Products Online Is Going Mobile
Paying For Products Online Is Going Mobile
In 2014, smartphone users who used their phones to make mobile payments for products or services was at 28 percent. Of these payments, 68 percent were to pay recurring monthly bills. The number of smartphone users who make point-of-sale purchases with their smartphones each year has remained steady at around 40 percent. But as mobile payment options become more popular, that number will start to rise.
The Problems with Paying Through Your Mobile Phone
Smartphone users often believe that using their phone is safer for paying bills, bank transfers and buying products rather than a computer. The truth is that your smartphone uses the same Internet as your desktop, and you have to be vigilant to keep your information safe.
When you pay a utility bill or buy a product through your smartphone, you are exposing your bank and vendor information to anyone who may be trying to tap into your connection to steal your data. While smartphones may be convenient to pay bills and buy products online, you still need to protect yourself from people who are on the lookout to steal personal identities and financial information.
 Protect Yourself When Using Your Smartphone
Protect Yourself When Using Your Smartphone
According to Bank of America, securing your smartphone screen with a strong password makes it difficult for criminals to get into your phone when connected to the Internet. Some banks and online vendors offer the ability to log into your accounts without having to expose your personal information. You should consider starting accounts with these types of business websites.
U.S. News and World Report recommends turning off the option on your phone that automatically connects to the closest cellular or WiFi Internet connection to prevent connecting to unsecured networks. You should also change your passwords frequently for all of your accounts to prevent criminals from becoming familiar with your accounts.
As more people start using their mobile phones to pay bills and buy products, the need to protect your phone is essential. Global IT offers a full computer security package with mobile phone protection services to keep your smartphone protected from criminals. The package protects against harmful malware and viruses, and covers multiple devices from your mobile phone to your computer or tablet.
https://info.globalit.com/wp-content/uploads/2016/04/146203-425×282-cell_hacking.jpg|https://info.globalit.com/wp-content/uploads/2016/04/smartphone-mobile-security.jpeg|https://info.globalit.com/wp-content/uploads/2016/04/enterprise-data-security-protection.jpg
Case Studies
Why you need to move to the Cloud
The Cloud sounds like some mystical place where data is held in golden vaults and retrieved by Microsoft certified angels. Well, perhaps the perception of the Cloud is not quite that dramatic, but many business owners do tend to avoid learning the facts about the cloud that could help their business and save them money.
 According to SiliconAngle.com, the cloud computing market is expected to exceed $79 billion by 2018. It is also interesting to note that one-quarter of all business executives who were polled said that if they could only move one function of their IT services to the Cloud, they would move data storage. People believe that the Cloud is so prominent that 32 percent of all Americans feel that cloud computing is the wave of the future, and it is a wave your company can ride to success.
According to SiliconAngle.com, the cloud computing market is expected to exceed $79 billion by 2018. It is also interesting to note that one-quarter of all business executives who were polled said that if they could only move one function of their IT services to the Cloud, they would move data storage. People believe that the Cloud is so prominent that 32 percent of all Americans feel that cloud computing is the wave of the future, and it is a wave your company can ride to success.
The Financial Benefits of Moving To the Cloud
According to WebRoot.com, the Cloud offers several financial benefits over buying onsite storage. When you use onsite physical storage, you have:
- Maintenance Costs
- Equipment Repair and Upgrade Costs
- Personnel Costs
With the Cloud, you do not have any of these costs to worry about anymore. The Cloud also does not require any initial capital purchases of equipment either. As long as your company has Internet-enabled computers, then you already have the equipment you need to use the Cloud.
Using the Cloud also eliminates the need to invest in backup equipment for your data, along with the costs associated with running redundant servers to prevent your network from going down. When you add up how much you spend on equipment alone for a computer network, you can understand how the Cloud saves you money.
The Operational Benefits of Moving To the Cloud
Oracle.com points out that being on a cloud system means that your company can grow at a natural pace, instead of being hampered by the need for more technology to accommodate your growth. When you are on the Cloud, you no longer have to figure technology costs into your business’ growth plans.
 Whether you intend to expand your operations throughout the country or around the world, using a cloud system means you never have to purchase additional equipment for each location. Any satellite office or main business location can tap into your company’s cloud service and be on the same network the rest of the company uses. In more ways than one, cloud computing takes all of the technology costs and worries out of growing your business to any size you want.
Whether you intend to expand your operations throughout the country or around the world, using a cloud system means you never have to purchase additional equipment for each location. Any satellite office or main business location can tap into your company’s cloud service and be on the same network the rest of the company uses. In more ways than one, cloud computing takes all of the technology costs and worries out of growing your business to any size you want.
Outsourcing Your Cloud Transition
The Cloud is a safe and secure place to use as your company’s computer network, but getting there can be a challenge. Remember that when you decide to transition to a cloud network, you are moving all of your company’s data to a brand new platform. It can take time, and it is not easy. Luckily, there are experts who can make the transition simple.
According to MSP Mentor, around 53 percent of all businesses that have moved to a cloud solution made the transition on their own. That means that 47 percent of companies preferred to allow professionals to make the transition for them. However, 50 percent of the companies that did it on their own said that they should have outsourced their transition to make the process easier and more comprehensive.
Global IT has a professionally managed data center that will host your cloud system and take your technical support calls 24-hours a day, and seven days a week. Global IT technicians are qualified and understand cloud transition that can make sure that your data is safely moved to your cloud solution, and that you are up and running as quickly as possible. Take advantage of everything the Cloud has to offer and make sure you have a professional organization make the transition for you.
https://info.globalit.com/wp-content/uploads/2016/04/corelynx_blog_5.jpg|https://info.globalit.com/wp-content/uploads/2016/04/417346-back-up-your-cloud-how-to-download-all-your-data.jpg|https://info.globalit.com/wp-content/uploads/2016/04/LearnMoreButton345x53_CloudService.png
Case Studies
Crypto-ransomware Virus Hits Kentucky Hospital
 When the world starts to hear about the exploits of a computer virus, it means the virus is performing some serious damage around the world. When ransomware was introduced, it took viruses to a whole new level. Ransomware is a virus that locks up your data files and then demands that you pay a ransom to have those files unlocked. It is difficult to understand how these transactions can take place without the FBI being able to track the offenders, these viruses are causing damage around the business world.
When the world starts to hear about the exploits of a computer virus, it means the virus is performing some serious damage around the world. When ransomware was introduced, it took viruses to a whole new level. Ransomware is a virus that locks up your data files and then demands that you pay a ransom to have those files unlocked. It is difficult to understand how these transactions can take place without the FBI being able to track the offenders, these viruses are causing damage around the business world.
Towards the end of 2014, the ransomware virus named Dridex started attacking banks, and ransoms were being paid to servers in secret locations all over the world. But now it looks like the virus developers are attempting to trap a broader audience as the new ransomware virus called Locky is attacking hospitals, using a method that would work with any type of organization anywhere in the world.
How Does Locky Work?
When Locky was first introduced, it was disguised as a macro on documents using older versions of Microsoft Word. Once a user downloaded the document, the macro would immediately go to work infecting one machine, or an entire network. Newer versions of Microsoft Word do not recognize the macro, so now the virus is delivered in a ZIP file that has to be opened to be activated.
 Once Locky is activated, it immediately creates copies of all of the documents on a server or desktop computer using the extension .locky. These documents are put into an encrypted file and the originals are deleted completely from the system. A ransom message then appears on the screen demanding a payment to a specific Internet address using an online form of payment called bitcoins. If the ransom is paid, a code is sent to unlock the files. If the ransom is not paid, the files are all deleted.
Once Locky is activated, it immediately creates copies of all of the documents on a server or desktop computer using the extension .locky. These documents are put into an encrypted file and the originals are deleted completely from the system. A ransom message then appears on the screen demanding a payment to a specific Internet address using an online form of payment called bitcoins. If the ransom is paid, a code is sent to unlock the files. If the ransom is not paid, the files are all deleted.
One Hospital Fought Back
Locky has been labeled by many security experts as one of the most lucrative ransomware viruses in existence. CryptoWall 3.0 is a ransomware virus that is said to have brought in $325 million dollars in ransoms, and Locky could be on its way to eclipsing that amount very soon. According to ThreatPost.com, experts have been able to detect 3,680 successful deployments of the Locky virus every hour since the virus was released in January. Victims seem powerless to do anything, but one hospital fought back.
One of Locky’s first big victims to publicly talk about their attack was Hollywood Presbyterian Medical Center in Los Angeles, California. Doctors could not use the computer system to treat patients, so they had to fax information back and forth with information providers and other hospitals around the world. The Locky ransom for this attack was initially reported to be $3.6 million. Administrators attempted to work around the virus, but it is alleged that the hospital finally paid $17,000 to get back online.
The Methodist Hospital in Henderson, Kentucky reported that it was hit by Locky and was able to get back online without paying the ransom. How did they do it? The administrators went through each computer one-by-one, including the servers, and scanned for the virus. When the found the virus, they removed it and loaded the backup files. The backup was not as recent as hospital officials would have liked, but the hospital publicly reported that the virus was gone and no ransom was paid.
Protecting Yourself from Locky
Locky arrives as an attachment to an email, the attachment then needs to be opened for the virus to be distributed. According to Blytheco.com, there are several ways for companies to protect themselves from viruses such as Locky. The first is to make sure you are using quality computer security or anti-virus software, which updates implementations constantly. While updated software may not be able to identify Locky right now, it can detect that there is something wrong with the attachment in the email.
The other way to protect your company from viruses like Locky is to develop a strong email policy that prohibits employees from opening suspect email attachments, and train your IT department to learn how to test attachments for viruses. Many companies have computers not attached to their networks that they use to open suspect attachments they cannot identify. Following these types of steps can help prevent your company from ever having to pay a faceless criminal a ransom for your own data.
For further protection:
https://info.globalit.com/wp-content/uploads/2016/04/LearnMoreButton345x53_Customers.png|https://info.globalit.com/wp-content/uploads/2016/04/LearnMoreButton345x53_Contactus.png|https://info.globalit.com/wp-content/uploads/2016/04/LearnMoreButton345x53_Need_help_Contact.png|https://info.globalit.com/wp-content/uploads/2016/04/locky-ransomware-100649480-primary.idge_.jpg|https://info.globalit.com/wp-content/uploads/2016/04/locky-ransom-1200.png|https://info.globalit.com/wp-content/uploads/2016/04/images.jpg
Case Studies
Global IT for Best Computer Support!
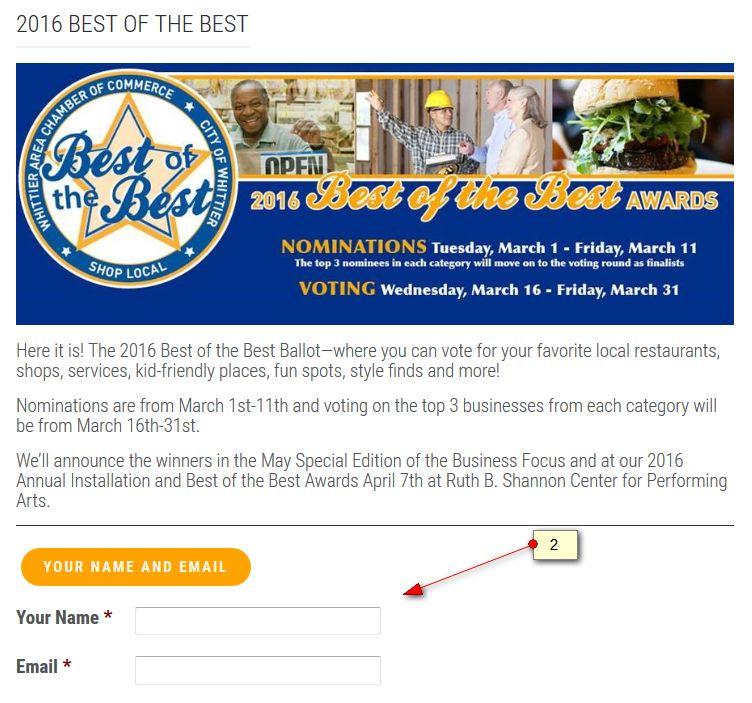
Pleasured to announce, that Global IT has been nominated for Best Computer Support in the Best of the Best Awards held by the Whittier Chamber.
We got nominated last year, but never received an award… help us make it this year!
It’s super easy and takes 2 minutes to do.
1. Go to www.whittierchamber.com/bestofthebest/ then follow these instructions.
Case Studies
When You Supply Google With Internet…
Global IT had the pleasure of working along side one of the biggest tech giants of all time, Google.
Friday last week, Google held Let’s Put Whittier on the Map and needed our high speed fiber internet to connect its guests online.

A few weeks leading up to the event Google contacted us, explaining how they were holding an event in our hometown and needed a hand with internet services. We were happy to help.
Our technicians set up an AirFiber X Antenna on our office roof facing in the direction of the venue, the Raddison Hotel. This wasn’t an ordinary antenna, it advances in noise isolation and beam performance, perfect for Point-to-point (PtP) bridging. This allowed us to bridge the gap between the two buildings by sending out our internet to the hotel.

The conference was a success with all 80 guests connecting online at once to complete workshops. Topics covered were how to grow your business online, get found on google search and maps, along with how to build your free website.
Google has been hosting Let’s Put Our Cities On the Map around the country since 2011. The purpose of the free program is to help small businesses establish themselves online to increase their customer base.
https://info.globalit.com/wp-content/uploads/2016/03/IMG_2750jn.jpg|https://info.globalit.com/wp-content/uploads/2016/03/shaun-installing-wireless-antenna.jpg|https://info.globalit.com/wp-content/uploads/2016/03/IMG_2753.jpg|https://info.globalit.com/wp-content/uploads/2016/03/IMG_2756gg.jpg
Case Studies
WIN Front Row Tickets to Fight Night In Los Angeles
Need a night out? Get your next one on us…
$300 in value!
WHERE: Bonnaventure Hotel
WHEN: March 26 at 6pm
WHO: You & a friend
HOW: Refer to win
Global IT is giving you the chance to win 2 VIP front row seats to Fight Night at the Bonnaventure Hotel in Los Angeles.
All you need to do is refer us to someone who would benefit from our IT services. Get them to contact us providing your name as a reference. It’s that easy.
The more you refer, the more times you can enter, increase your chances of winning.
Click here for more information.
Contact us.
Case Studies
Transferring domain(s) away from Global IT Communications, Inc.

In order to transfer a domain away from Global IT, you will have to complete the following steps:
- Ensure all administrative and technical contact information is up to date.
- Request a Global IT administrator to turn off/cancel Protected Registration or Private Registration, if applicable. (Included with administrative fee*)
- Once requested a Global IT administrator will verify the domain is unlocked. (Included with administrative fee*)
- Initiate the domain transfer through your new domain registrar.
- If applicable, request an authorization code from Global IT (Included with administrative fee*)
- Authorize transfer with your new registrar.
- Receive email notification from our registrar.
- Your new registrar will receive email notification from Global IT registrar of the transfer’s acceptance or rejection
*$35 administrative fee
https://info.globalit.com/wp-content/uploads/2016/03/3dd8499.jpg|https://info.globalit.com/wp-content/uploads/2016/03/transfer.png
Case Studies